This Bing flaw let hackers change search results and steal your files
A serious bug in Microsoft’s Azure platform could have let hackers switch up search results and steal the files of millions of users, a security firm has found.

By
Alex Blake
March 31, 2023 4:19AM 
A security researcher was recently able to change the top results in Microsoft’s Bing search engine and access any user’s private files, potentially putting millions of users at risk — and all it took was logging into an unsecured web page.
The exploit was discovered by researcher Hillai Ben-Sasson at their team at Wiz, a cloud security firm. According to Ben-Sasson, it would not only allow an attacker to change Bing search results but would also grant them access to millions of users’ private files and data.
Dubbed BingBang by the research group, the vulnerability centered on Microsoft’s Azure Active Directory, which is used by enterprises to manage user identities and access to apps. Unfortunately, if an app is misconfigured, any Azure user in the world can log into it without the proper credentials.
Shockingly, the researchers noted in a technical analysis of the bug that up to 25% of all multi-user apps they scanned were vulnerable — including a Microsoft app named Bing Trivia.
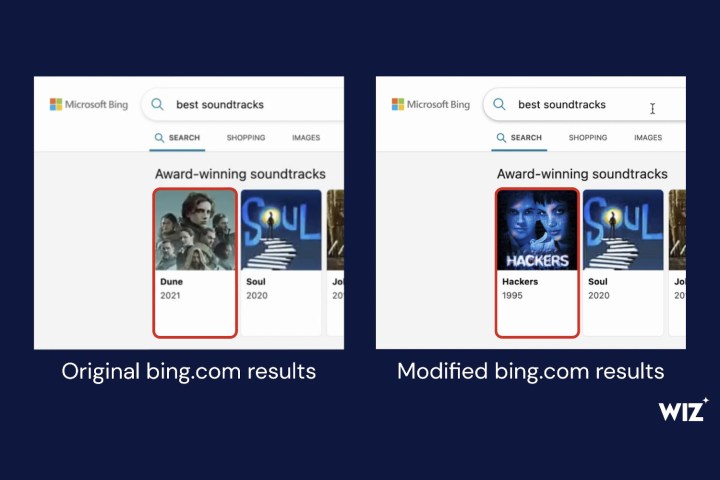
After exploiting the flaw to log into the Bing Trivia app, the Wiz team found a content management system (CMS) tied to Bing.com that was controlling the search engine’s live results. With a touch of humor, they then altered one of the entries, changing the top result for ‘best soundtracks’ from the Dune score to that from the 1995 movie Hackers.
However, there’s nothing funny about what this flaw implies. As the researchers explained, “a malicious actor landing on the Bing Trivia app page could therefore have tampered with any search term and launched misinformation campaigns, as well as phished and impersonated other websites.”
Stealing private files and emails
 Wiz
WizWhat’s more, the researchers were able to add a harmless cross-site scripting (XSS) payload into Bing while they were logged in. This was able to run as expected, without interference. After reporting the issue to Microsoft, the researchers tried modifying this XSS payload to see what was possible.
Because Bing integrates with Microsoft 365, the Wiz team was able to create a script that could potentially steal a logged-in user’s access tokens, granting them access to that user’s cloud data. That could include Outlook emails, calendars, Teams messages, OneDrive files, and more.
Put together, that means a hacker could have the power to redirect Bing search results to a malicious website, and at the same time harvest private data from any user logged in on a Microsoft 365 account. All from exploiting a simple login vulnerability.
Fortunately, the researchers immediately reported the flaw to Microsoft and it was patched shortly afterward, resulting in a $40,000 bug bounty reward. Yet it remains an alarming example of how little effort can be required to steal private data from millions of unsuspecting users.
Editors' Recommendations
This new Microsoft Bing Chat feature lets you change its behavior Check your inbox — Microsoft just sent out the first wave of ChatGPT Bing invites Hacker steals 1 billion people’s records in unprecedented data breach Microsoft will never win the search engine wars by forcing people to use Bing Bing, Windows search evolve into new, cross-platform Microsoft SearchNetgear router bug let hackers steal classified documents on drones, tanks
Netgear says exploit that led to stolen documents was fixed a long time ago
A U.S. Air Force MQ-9 Reaper drone. EthanMiller/GettyImages
Hackers have managed to gain entry to classified documents on an Air Force captain's computer after they exploited a known flaw in a Netgear router. Although the full extent of the data theft is still being quantified, the maintenance documents for the MQ-9 Reaper drone were stolen, as well as training manuals for the M1 Abrams tank, and defense tactics for tackling improvised explosive devices, were all found for sale on the dark web, Ars Technica reported. Netgear has since clarified to Digital Trends that the exploit used in the attack was fixed a long time ago in several firmware updates to its hardware.
Cortana flaw enables hackers to load malicious websites from the lock screen
Two independent Israeli researchers recently discovered that anyone with access to a Windows 10 PC could use Cortana and a USB-based network adapter to download and install malware even if the machine remained locked. This was accomplished using voice commands directed to Cortana, which could load up a malicious website in a browser without unlocking Windows. The PC could also be moved to a wireless network controlled by the hacker.
The two researchers, Tal Be'ery and Amichai Shulman, presented their method in a session called, "The Voice of Esau: Hacking Enterprises Through Voice Interfaces" during the Kaspersky Analyst Security Summit in Cancun, Mexico, last week. Their attack relied on Cortana's ability to keep the microphone active at all times to receive voice commands, especially PCs that aren't restricted to a single user's voice. The attack also required physical access to the target PC.
In their scenario, a hacker could sit down in front of a locked Windows 10 PC and insert a network adapter into one of the USB slots. After that, the hacker could verbally tell Cortana to open the web browser and head to any specific HTTP-based address that doesn't rely on a secure connection (HTTPS means the connection is encrypted). The inserted adapter receives the outgoing command but directs the web browser to a malicious website instead.
The malicious destination is designed to download malware to the machine even though it's still locked. After that, the PC is at the mercy of the hacker. As previously stated, a hacker with physical access to the Windows computer can switch to a wireless, malicious network through the USB adapter: just click on the destination using a mouse even though the PC remains locked.
Windows 10 provides several settings regarding Cortana. For starters, device owners can toggle on or off the ability for the virtual assistant to respond to the "Hey Cortana" voice command. There is also a checkbox to prevent the device from sleeping when it's plugged in so Cortana can respond to commands. Most importantly, there are two main settings for voice command acceptance: Let Cortana respond to anyone or lock Cortana to one specific voice.
That is not all. There is a specific setting for the lock screen, enabling users to enable or disable voice commands while the PC remains locked. Windows 10 also provides a keyboard shortcut you can toggle to disable or enable Cortana commands after pressing the Windows logo key and the "C" key simultaneously.
"We still have this bad habit of introducing new interfaces into machines without fully analyzing the security implications of it," Be'ery said. "Every new machine interface that we introduce creates new types of vehicles to carry an attack vector into your computer."
Ultimately, Microsoft resolved the issue discovered by Be'ery and Shulman. Browser-based commands made to Cortana on the lock screen now go directly to Bing, the company's search engine. But because Cortana responds to other commands, the duo is currently investigating how these commands can be used for malicious purposes as well.
Google may soon let you test your internet speed straight from search results
As consumers become increasingly aware of the importance of a speedy internet connection for getting the most out of the web's broad spectrum of services, so more and more users are conducting Google searches for tools that test their provider’s performance.
Finally waking up to the fact, the Mountain View company is reportedly trialing its own internet speed service, embedding it at the top of relevant search inquiries.

 Koichiko
Koichiko