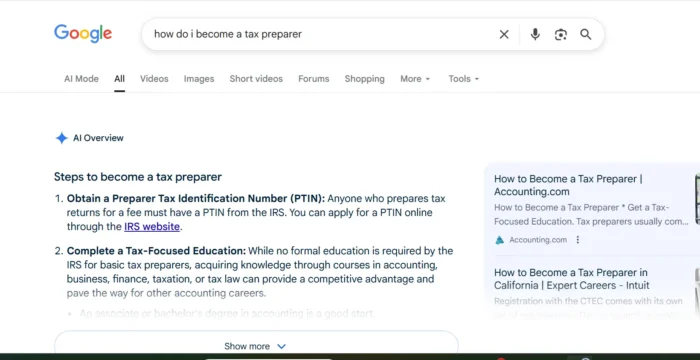
U.S. officials link North Korean hackers to $615 million cryptocurrency heist
North Korean state-backed hacking collective Lazarus Group is linked to the theft of $615 million in digital assets, U.S. officials allege.

A photo illustration showing the North Korean flag and a computer hacker.
Budrul Chukrut | Sopa Images | Lightrocket | Getty Images
North Korean state-backed hacking collective Lazarus Group is linked to a massive cryptocurrency hack that led to the theft of $615 million in digital assets, U.S. officials allege.
The Treasury Department's Office of Foreign Assets Control on Thursday announced new sanctions against an ethereum wallet belonging to Lazarus.
According to crypto researchers, the identified wallet contains funds related to an attack on the Ronin Network, which supports the popular blockchain game Axie Infinity. More than $600 million worth of ether and USDC tokens were stolen in the attack.
Hackers exploit what's known as a blockchain "bridge," which allows users to transfer their digital assets from crypto network to another. Bridges are an increasingly popular tool in the rapidly-growing world of "decentralized finance," or DeFi.
The newly announced sanctions prohibit U.S. individuals and entities from making transactions with the identified ethereum account to make sure the hackers can't "cash out" any funds they may hold with American crypto exchanges, blockchain analytics firm Elliptic said in a blog post.
Chainalysis, another crypto research group, said the attribution to Lazarus highlights the importance of "how DPRK-affiliated threat actors exploit crypto, and better security for DeFi protocols."
Lazarus, which is believed to be operated by the North Korean state, has been associated with several major cyberattacks over the years, including a 2014 hack on Sony Pictures and the 2017 WannaCry ransomware attacks.
North Korea has attempted to use crypto as a way to evade U.S. sanctions on numerous occasions, according to cybersecurity experts, raising concerns about the possible use of digital assets for Russian sanctions evasion amid the Ukraine war.
Earlier this week, Virgil Griffith, a 39-year-old American crypto expert, was sentenced to five years in prison for helping North Korea use virtual currencies to evade sanctions.
Proponents of cryptocurrencies say they are an ineffective tool in laundering ill-gotten gains, since activity is recorded on a public ledger known as the blockchain.
However, criminals have a number of techniques at their disposal to launder crypto, according to Elliptic. The company said internal analysis suggests the Ronin attacks "managed to launder 18% of their stolen funds" as of Thursday.
Hackers initially swapped stolen USDC tokens for ether through unregulated decentralized exchanges to prevent it from being seized, but then laundered almost $17 million of the proceeds through centralized exchanges like FTX and Huobi.
They subsequently used what's known as a "mixer," a service that aims to obscure the trail of funds by mixing streams of potentially identifiable crypto transactions with others. More than $80 million has been sent through this mixing service, called Tornado Cash, according to Elliptic.

 FrankLin
FrankLin