Your Data Protection Checklist
Data is the lifeblood of modern businesses that enables organizations to drive innovation. However, with the increasing reliance on data […] The post Your Data Protection Checklist appeared first on ReadWrite.

Data is the lifeblood of modern businesses that enables organizations to drive innovation. However, with the increasing reliance on data comes the need to protect it from various risks, including data breaches, cyberattacks, regulatory violations, etc.
Organizations must adopt a proactive approach to data protection to safeguard sensitive information and maintain the trust of customers and stakeholders. In this article, you’ll find robust data protection measures organized into a checklist that will assist your organization in bolstering your data protection practices.
1. Review the Data Your Business Collects
The first step to protecting data is to know all the data your business collects, where they are coming from, where they are stored, and how they are used. Categorizing the data you collect enables you to adopt a risk-based approach to data security and prioritize your efforts accordingly.
However, this would be impossible without first ensuring visibility and clarity. First, ensure that nothing goes under the radar; every endpoint must be monitored to avoid leakages. Number two is that you must assess the necessity of collecting each type of data. This transparency helps you to avoid gathering excessive information, which increases the risk of data breaches.
2. Evaluate Regulatory Compliance Requirements
Even if your business is domiciled in a region where there is no clear data protection regulation, you can be certain that it’s coming to you soon. Violating laws on protecting personal data leads to serious legal and financial sanctions that even big tech companies are not exempt from.
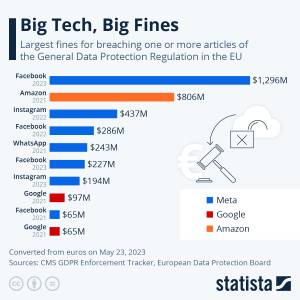
Source: Statista
Therefore, you must identify the data protection requirements that are relevant to you. Businesses that work across borders might find this challenging because various laws may be applicable. So, it’s important to stay informed on the latest updates to compliance obligations.
3. Designate a Data Protection Officer (DPO)
Besides your cybersecurity team, an employee should be directly responsible for ensuring data protection compliance throughout the organization, especially by enforcing the company’s privacy policy.
Under certain criteria, regulations such as the GDPR mandate a DPO’s appointment. However, even if it is optional, you may consider appointing an independent and impartial advisor that will supervise data protection governance in the organization.
They should have expertise in data privacy and security practices and a solid grasp of business processes and industry specifics.
4. Monitor Your Data Life Cycle
Data protection is not a one-time activity. Instead, data must be monitored throughout its life cycle to ensure that it is handled responsibly and protected from unauthorized access at every point.
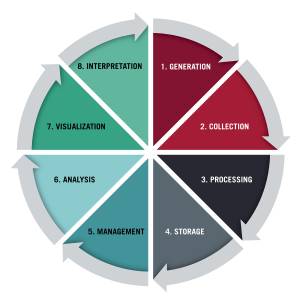
Source: Harvard Business School
This ongoing and multi-faceted process requires heightened vigilance, transparency, and commitment to data protection best practices. Ultimately, real-time monitoring aims to secure all endpoints and avoid leakages.
5. Enhance Detection Capabilities
You need an integrated and cloud-based data detection and response solution that protects sensitive data from undue exposure and prevents any type of data loss by monitoring endpoints intelligently in real-time.
It helps to explore AI-based behavioral analytics to detect anomalies and automatically trigger an incident response workflow due to a combination of content analysis, contextual awareness, and policy-based rules.
6. Create a Data Breach Reporting Structure
The GDPR, for instance, mandates that all data breaches should be officially reported within 72 hours. Whether this mandate applies to your organization or not, all businesses should have a clear data breach reporting hierarchy to ensure a swift and coordinated response.
For one, the criteria for reporting and classifying different types of incidents and their severity levels should be established and clear to all. There should also be explicit communication protocols so that reports can reach the right individuals promptly.
Particularly, key internal and external stakeholders who need to know about a data breach (depending on its severity) should be well informed. This may include senior management, legal team, public relations, regulatory authorities, affected data subjects, etc. And everyone should know their roles and responsibilities concerning the breach.
7. Create and Enforce a Privacy Policy
Besides the need to comply with regulations, having your own policy helps establish customer trust. If made public, it serves as a declaration of your organization’s commitment to protecting its users’ and customers’ privacy and personal data.
However, what matters most is enforcement; a privacy policy must be enforceable and should cover key components such as data collection and usage, consent mechanism, data security measures, rights of data subjects, cookie policy, employee training, etc.
8. Regularly Assess Third-Party Risks
Third-party partners, vendors, and suppliers are often sources of data leakages, especially when you can’t verify that they take data protection as seriously as you do. As such, without assumptions, you must regularly assess third-party security practices and risks to ensure that the data you share with them is in safe hands.
Assessing third-party risks is critical for incident response, business continuity, and disaster recovery. So, all decision-making concerning contractual obligations must be risk-based.
9. Conduct Regular Audits
Besides continuous monitoring, regular full-scale audits ensure that your organization’s data-handling practices align with internal policies and external regulations. They are meant to objectively assess data protection measures and help identify potential vulnerabilities and areas for improvement. Some tips for conducting an audit include the following:
Assemble an audit team Develop a plan that includes a timeline, procedures, and documentation Interview key personnel and review relevant documentation Assess data security measures Review incident logs Evaluate employee training and awareness Identify non-compliance and risks Follow-up and monitor progressConclusion
As data continues to be a valuable asset and a potential liability, ensuring robust data protection practices is not just an option but a strategic imperative for every organization. By following this comprehensive checklist, your organization can strengthen its overall resilience against data threats and minimize the risks of breaches.
Featured Image Credit: Christina Wocintechchat; Pexels; Thank you!

 AbJimroe
AbJimroe