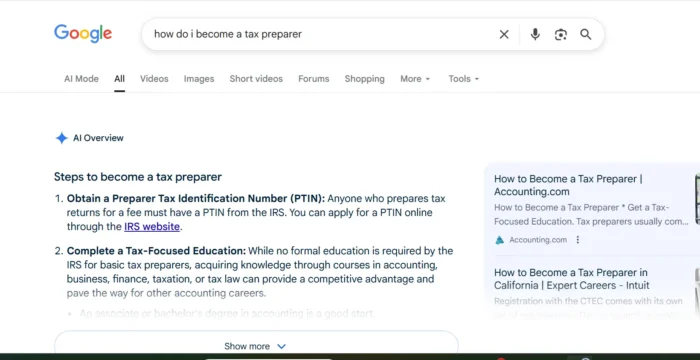
Here’s the major mistake one LAPSUS$ hacking victim made
Okta raised eyebrows after confirming it was targeted by hackers long after the breach occurred. The digital security firm now admits it made a mistake.

Digital security authentication company Okta raised eyebrows when it confirmed it was targeted by Microsoft and Nvidia hackers, LAPSUS$, around two months after the breach occurred.
The wait between the initial period of the cyber security incident and the official acknowledgment of the hack caused serious concern among security researchers and the technology community. Now, Okta has published an FAQ regarding the situation where it admits the firm made a mistake.
 Stock Depot/Getty Images
Stock Depot/Getty ImagesLAPSUS$ claimed to have gained access to Okta’s systems through infiltrating one of its customers, Sitel, in January. Okta confirmed as much when it stated that it detected suspicious activity on January 20. It says it received a “summary report about the incident from Sitel” on March 17.
However, Okta only confirmed the hack after LAPSUS$ released sensitive images last week. The company, which provides authentication technology to some of the largest companies in the world — including government agencies — has now responded to the severe backlash in an FAQ:
“We want to acknowledge that we made a mistake. Sitel is our service provider for which we are ultimately responsible.
“In January, we did not know the extent of the Sitel issue – only that we detected and prevented an account takeover attempt and that Sitel had retained a third party forensic firm to investigate. At that time, we didn’t recognize that there was a risk to Okta and our customers. We should have more actively and forcefully compelled information from Sitel.
“In light of the evidence that we have gathered in the last week, it is clear that we would have made a different decision if we had been in possession of all of the facts that we have today.”
Elsewhere, leaked documents shared with Wired by independent security researcher Bill Demirkapi call into question the strength, or apparent lack thereof, of Sitel’s security system and mitigation responses, as well as showcasing “apparent gaps in Okta’s response to the incident.”
According to the report, LAPSUS$ relied on tools such as Mimikatz, which is designed to extract passwords, to gain further access to Sitel’s systems.
“The attack timeline is embarrassingly worrisome for Sitel group,” Demirkapi stressed. “The attackers did not attempt to maintain operational security much at all. They quite literally searched the internet on their compromised machines for known malicious tooling, downloading them from official sources.”
Strong backlash
In any case, both security researchers and Okta’s own clients have found fault with how the firm has responded to the hack.
For example, as reported by Computing.co.uk, Tenable CEO Amit Yoran, which is a cybersecurity firm as well as an Okta customer, provided a strongly-worded statement addressed to Okta via LinkedIn:
“You either didn’t investigate properly or disclose the breach in January when it was discovered. When you were outed by LAPSUS$, you brushed off the incident and failed to provide literally any actionable information to customers. LAPSUS$ then called you out on your apparent misstatements. Only then do you determine and admit that 2.5% (hundreds) of customers’ security was compromised. And still actionable detail and recommendations are nonexistent.
“No indicators of compromise have been published, no best practices and no guidance has been released on how to mitigate any potential increase in risk. As a customer, all we can say is that Okta has not contacted us.”
Demirkapi echoed the sentiments of the aforementioned open letter when he initially commented on the incident last week. “In my opinion, it looks like they’re trying to downplay the attack as much as possible, going as far as directly contradicting themselves in their own statements,” he said.
Meanwhile, seven hackers associated with LAPSUS$ (aged 16 to 21) were apparently arrested last week in London, according to Wired. However, they were all eventually released without being formally charged.
LAPSUS$ has made quite an entry into the hacking community. We initially found out about them via its 1TB Nvidia hack, which was recently followed by an infiltration of Microsoft’s systems. As for the latter firm, it has already reportedly seen source codes for Cortana and its Bing search engine being leaked.

 Konoly
Konoly