Vulnerabilities in Two ThemeForest WordPress Themes, 500k+ Sold via @sejournal, @martinibuster
Two WordPress themes on Themeforest were found with medium to high threat vulnerabilities. One remains unpatched and at risk. The post Vulnerabilities in Two ThemeForest WordPress Themes, 500k+ Sold appeared first on Search Engine Journal.

A vulnerability advisory was issued about two WordPress themes found on ThemeForest that could allow a hacker to delete arbitrary files and inject malicious scripts into a website.
Two WordPress Themes Sold On ThemeForest
The two WordPress themes with vulnerabilities are sold on ThemeForest and together they have over a half million sales.
The two themes are:
Betheme theme for WordPress (306,362 sales) The Enfold – Responsive Multi-Purpose Theme for WordPress (260,607 sales)Betheme Theme for WordPress Vulnerability
Wordfence issued an advisory that The Betheme theme contained a PHP Object Injection vulnerability that was rated as a high threat.
Wordfence was discreet in their description of the vulnerability and offered no details of the specific flaw. However, in the context of a WordPress theme, a PHP Object Injection vulnerability usually arises when a user input is not properly filtered (sanitized) for unwanted uploads and inputs.
This is how Wordfence described it:
“The Betheme theme for WordPress is vulnerable to PHP Object Injection in all versions up to, and including, 27.5.6 via deserialization of untrusted input of the ‘mfn-page-items’ post meta value. This makes it possible for authenticated attackers, with contributor-level access and above, to inject a PHP Object. No known POP chain is present in the vulnerable plugin.
If a POP chain is present via an additional plugin or theme installed on the target system, it could allow the attacker to delete arbitrary files, retrieve sensitive data, or execute code.”
Has Betheme Theme Been Patched?
Betheme Theme for WordPress has received a patch on August 30, 2024. But Wordfence’s advisory isn’t acknowledging it. It’s possible that the advisory needs to be updated, not sure. Nevertheless, it’s recommended that users of the Enfold theme consider updating their theme to the newest version, which is Version 27.5.7.1.
The Enfold – Responsive Multi-Purpose Theme for WordPress
The Enfold Responsive Multi-Purpose WordPress theme contains a different flaw and was given a lower severity rating of 6.4. That said, the publisher of the theme has not issued a fix for the vulnerability.
A Stored Cross-Site Scripting (XSS) was discovered in the WordPress theme from a flaw originating in a failure to sanitize inputs.
Wordfence describes the vulnerability:
“The Enfold – Responsive Multi-Purpose Theme theme for WordPress is vulnerable to Stored Cross-Site Scripting via the ‘wrapper_class’ and ‘class’ parameters in all versions up to, and including, 6.0.3 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.”
Enfold Vulnerability Has Not Been Patched
The Enfold – Responsive Multi-Purpose Theme for WordPress has not been patched as of this writing and remains vulnerable. The changelog documenting the updates to the theme shows that it was last updated in August 19, 2024.
Screenshot Of Enfold WordPress Theme’s Changelog
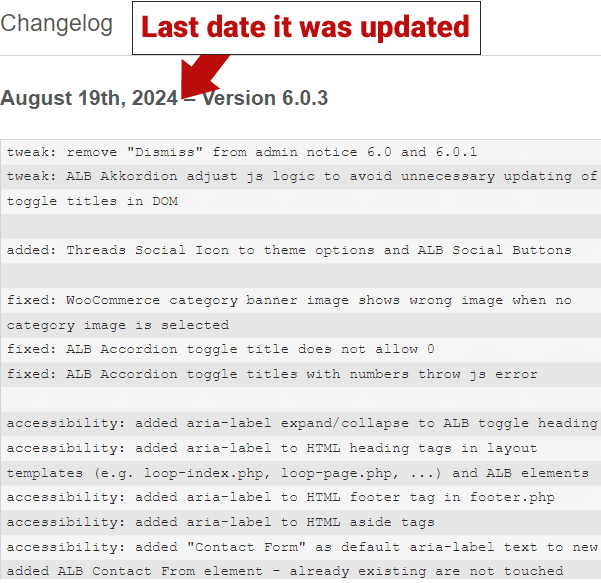
The Enfold – Responsive Multi-Purpose Theme for WordPress has not been patched as of this writing and remains vulnerable.
Wordfence’s advisory warned:
“No known patch available. Please review the vulnerability’s details in depth and employ mitigations based on your organization’s risk tolerance. It may be best to uninstall the affected software and find a replacement.”
Read the advisories:
Betheme <= 27.5.6 – Authenticated (Contributor+) PHP Object Injection

 ValVades
ValVades