Risks, Threats, and Security Challenges Posed in Moving to the Cloud
Moving to the cloud has become a common trend for businesses in various industries – and the benefits of cloud computing are undeniable. Cloud migrations typically allow organizations to reduce operational costs, improve scalability and increase the accessibility of...
Moving to the cloud has become a common trend for businesses in various industries – and the benefits of cloud computing are undeniable. Cloud migrations typically allow organizations to reduce operational costs, improve scalability and increase the accessibility of data.
However, security is a significant consideration in cloud computing environments, and organizations need to be aware of the risks, threats, and challenges they may face when making the switch.
Cyber Attacks
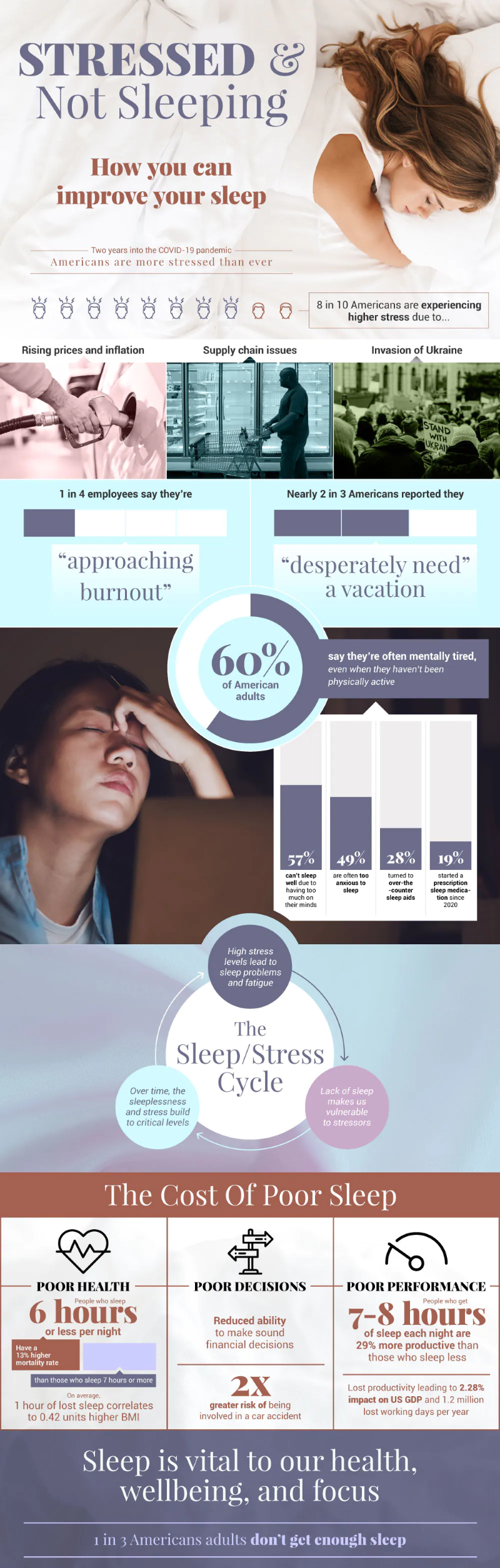
Cyber attacks are among the most significant risks associated with operating in the cloud. These attacks disrupt a business’s underlying infrastructure and can substantially impact its reputation.
Cloud environments are a high risk in business settings because they are exposed to the internet with multiple points of entry, making them more vulnerable. Threat actors can use various methods to launch attacks, such as exploiting unpatched vulnerabilities, phishing techniques, or brute-force attacks.
To mitigate these attacks, businesses should use a defense in depth (DiD) security approach that includes firewalls, intrusion detection systems, and strong passwords.
Insider Risks
Insider risks posed by individuals within an organization who intentionally or unknowingly cause harm to databases, connected systems, or company resources. Most of these risks are from simple misconfigurations or accepting default settings which tend to mean security is turned off. Security by design is one thing but we need to move to security by default. Most employees are focused on getting the job done and they take the easy path which tends to be the highest risk.
One of the reasons why insider risks pose such a significant risk is that they often have privileged access to sensitive data. Whether it’s because of their job responsibilities or level of authority within the organization, these insiders have dangerous levels of access to company resources.
Moving your company’s operations to the cloud can increase the risks posed by insider threats. Since cloud providers often have multiple customers on the same servers, there is a greater risk of another customer’s data being compromised.
In addition, cloud providers often have a higher level of trust in their employees than other organizations, which makes it easier for insiders to access sensitive data.
Insecure APIs
APIs (Application Programming Interfaces) are the backbone of cloud computing ecosystems. APIs make it easy for businesses to interact with third-party solutions and cloud service providers. However, while APIs offer increased convenience, they also pose security challenges.
Vulnerabilities like SQL injection, cross-site scripting (XSS), and injection-based attacks are common in insecure APIs. Insecure APIs are a significant threat to businesses because their gateways act as access points to other cloud resources which, when compromised, could result in a catastrophic enterprise-wide data breach.
API misconfiguration occurs when there’s a lack of understanding of how the API works or poor implementation of its security measures. For example, failing to enable authentication, allowing unrestricted access, or not encrypting API requests can leave an organization vulnerable to attack.
To protect against API misconfiguration, organizations should deploy APIs built on secure and trusted frameworks with proper configuration settings.
Account Hijacking
Account hijacking is when the attacker gains unauthorized access to an account by stealing its credentials. This can be done through various methods, including phishing attacks, malware, social engineering, brute force attacks and even insider threats.
The attacker can then use the account to access sensitive information or commit malicious activities such as identity theft or fraud.
One reason why account hijacking is a security challenge in the cloud is that many businesses and their employees use weak passwords that are easy to bypass. This makes it easier for an attacker to gain access to an account.
Many employees will also use the same password across multiple accounts. If one account is compromised, it can lead to a domino effect, where all other accounts with the same password are accessible.
Compliance and Legal Risks
When businesses migrate to the cloud, they are subject to various legal and compliance risks. These include data privacy laws, intellectual property rights, data localization requirements, and industry-specific regulations.
As companies store and transfer sensitive information through a third-party vendor, data breaches and unauthorized access are always possible. With numerous compliance regulations and data privacy laws in place, ensuring that cloud service providers comply with these regulations can be difficult.
Companies need to ensure that their cloud service provider has proper security measures in place and is compliant with relevant standards such as HIPAA, GDPR and other regulatory compliance standards.
Advanced Persistent Threats
Advanced persistent threats (APTs) are increasingly common in the cloud. APTs are sophisticated attacks that target specific organizations or individuals over a long period of time, with the attacker often remaining undetected for months or even years.
APTs can be used to steal data, disrupt operations and sabotage systems. Organizations should implement multi-factor authentication to protect against these threats, regularly patch their systems, and monitor activity for suspicious behavior.
Additionally, organizations should use cloud-based security tools such as Privileged Access Management (PAM) and data loss prevention (DLP) solutions to help detect and mitigate threats in real-time.
Data Loss and Service Downtime
Data loss and downtime are other common risks associated with cloud computing. Data loss can occur due to natural disasters, malicious attacks, or human errors. Downtime typically occurs when there is a disruption in service due to maintenance or an outage on the part of the cloud service provider.
Organizations should ensure that their cloud service providers have adequate measures to prevent data loss and downtime. This includes having a reliable backup system, proper authentication protocols, and real-time monitoring systems.
Additionally, organizations should consider investing in a third-party cloud service provider that offers disaster recovery services to ensure data remains safe even during an outage.
Multi-Tenant Vulnerabilities
Multi-tenant cloud computing can create vulnerabilities that attackers can exploit. Multi-tenancy refers to the practice of multiple users or organizations sharing a single instance of an application or service, which is hosted on the same hardware and managed by the same provider.
Since all users are on the same network, any security vulnerabilities in one tenant’s environment can potentially be exploited by an attacker to gain access to other tenants’ data.
To protect against this risk, organizations should ensure that their cloud service provider has adequate security measures, including protected RDP connections, firewalls, encryption, and strong authentication and authorization using solutions such as privileged access management .
Organizations should also deploy intrusion prevention systems to detect and respond to any malicious activity on their networks.
Limited Visibility and Control
When companies migrate to a cloud-based environment, they lose visibility and control over their data and resources. This can be problematic as organizations may not be aware of any potential security risks or incidents within the cloud platform.
Organizations should ensure that they have adequate monitoring and logging systems in place to detect any suspicious activity or unauthorized access. They should also establish a well-defined policy for cloud security and ensure that their cloud service providers have proper authentication protocols and access controls in place.
Another way to ensure visibility and control over cloud resources is to invest in a third-party security provider that offers secure hosting, monitoring, and reporting services. This will help organizations gain better insight into their cloud environment and help them detect any potential security issues before they become significant problems.
Take Proactive Steps to Minimize Security Risks in the Cloud
The cloud can be a powerful tool for organizations, but it also comes with risks. To protect against these threats, organizations should ensure they deploy the right security measures and invest in cloud-based security solutions.
By taking the necessary steps to secure their cloud environment, organizations can ensure that their data and resources remain safe while enjoying the benefits of cloud computing.

 Troov
Troov